15th Signal + Draht Congress Migration, innovation and cybersecurity in command, control and safety systems
Text: Rainer Knewitz,
Design: Tim Meinken
Photos: Thomas Pieruschek
Digitisation is gaining ground on the railways and bringing with it hope for an attractive future. At the same time, however, it would appear that technological progress is being slowed down by two opposing poles: legacy technologies and cybersecurity. A further factor is that the new role of registered inspector and the German Federal Act on IT Security are creating new framework conditions for operators and manufacturers.
At the 15th International SIGNAL+DRAHT congress held in Fulda (Germany), 15 presentations were made under the overall title of “Modern command, control and safety systems facing the divergent pulls of migration, innovation and cybersecurity”. The speakers dealt with strategies, concepts and possible solutions for dealing effectively with the challenges in the present environment. The event was attended by just short of 300 participants from the international railway world.
The two main themes at the congress were “migration and innovation” and “cybersecurity”. There were also three presentations on par-ticularly interesting special topics. The sessions were chaired by the two chief editors of SIGNAL+DRAHT, Dipl.-Phys. Reinhold Hundt and Ing. August Zierl.

Content
- Challenges for railways running local services
- Challenges faced by Swiss Federal Railways
- Challenges faced by Austrian Federal Railways (ÖBB)
- The strategic concepts for information technology at DB Netz
- Challenges regarding training and personnel
- Migration, taking the example of electronic interlocking systems
- Field programmable gate arrays
- Germany’s new law on IT security – requirements for transport companies
- Importance of the German Federal Act on IT Security for critical infrastructures, using the railway industry as an example
- Role of IT security in railway operation
- IT security: Threat situation in practice
- Panel discussion
- Safety meets security – Strategies for documenting evidence
- New legislation creates the role of registered inspector in the railway industry
- Distributed power provision (DPP) – Flexible power supply as an important element in a decentralised interlocking technology archi-tecture
- Fibre-optic sensor systems in the railway environment – opportunities and challenges
Challenges for railways running local services
Dipl.-Ing. Ramón Uhrhan, Berliner Verkehrsbetriebe, reported on investigations carried out by his company into the introduction of com-munication-based train control (CBTC) in conjunction with the extension and renewal of Line 5 of the Berlin U-Bahn.
The Berlin U-Bahn has a total line length of 146 km, making it the fifth-largest metro network in Europe, with more than 500 million pas-senger journeys per year. The current traffic volume is handled by 35 interlocking units (31 of them relay-operated and four of them electronic). The flow of trains is controlled by spacing them out over fixed distances with lineside signals. Line 5 currently operates between Alexanderplatz and Hönow and is to be extended as far as Hauptbahnhof along a new section of line scheduled for opening in 2020. In the five years following that, the existing route is to be renewed, whereby the public-service contract makes provision for the current technical systems to be retained. It is reckoned that demand on Line 5 will grow steeply in the long run.
Since 2013, the train-protection department at Berliner Verkehrsbetriebe has been looking intensively into a possible modernisation of the train-protection equipment. It has been assisted in this by several workshops for pooling of experience from various equipment manufacturers and is currently working on drawing up a concept for a new approach to train protection. All the application conditions are also being filtered in order to ensure generalised deployment on more than one route. This includes, amongst other things, running on the surface and underground and the appropriate mixed operation of differently equipped train sets.
As things stand at present, there would appear to be no alternative to keeping trains running while performing a system change. That is going to make it necessary to have two sets of equipment fitted at least on the infrastructure side. Other issues are expanding radio com-munications and equipping the trains or at least having them prepared in advance for the use of CBTC at the time new orders are placed. It is hoped that this approach will leave more scope for reacting to changes and will also stimulate competition.
The concept envisages leaving the operational command and control systems and also the interlocking equipment more or less as they are and limiting the renewal of the train-protection equipment to the introduction of the communication-based system while reducing the number of signals. In order to make sure that the modern train-protection system remains fit for the future, the aim being pursued is to keep the subsystems clearly apart from one another but with knowledge of interfaces “within the operation”.
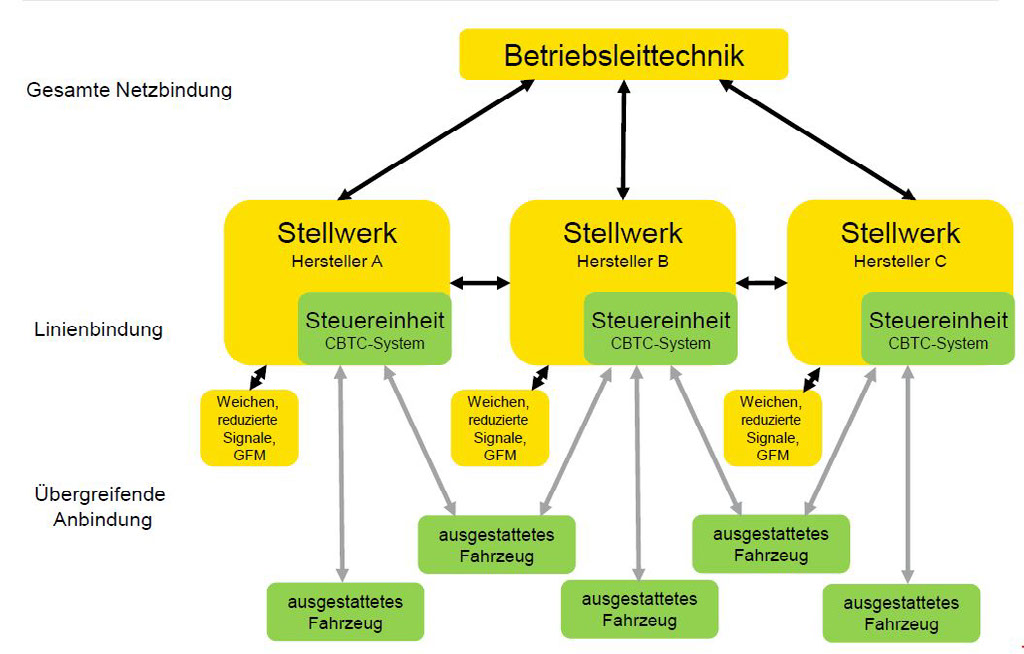
It is hoped that through using CBTC it will be possible not only to set up bi-directional connections to and from the trains but also to introduce dynamic adaptations to the driving profiles and headway adjustments, so that these can be better matched to requirements. Both of these measures are necessary in order to be able to handle the expected growth in the transport volume. In replying to questions from the audience, Ramón Uhrhan explained that shifting the safety intelligence to the vehicles had indeed been considered, but that that particular alternative was not being taken any further. For the time being, an open-source approach was not considered a priority.
Challenges faced by Swiss Federal Railways
Dipl.-Ing. Martin Messerli (SBB) stated that his company’s 518 interlocking units with more than 70 000 switched devices were making a crucial contribution to safety, automation and centralisation, but that they were also responsible for approximately 75% of all disruptions due to equipment and for around 10% of all the minutes of train delays. Automation had already gone a long way, with more than 90% of the switched devices being operated from one of the four operating control centres. The Swiss Federal Office of Transport had determined that ETCS was to be the target system for the Swiss standard-gauge network. In addition to equipping individual lines, implementation of ETCS Level 2 was taking place in two phases:
- equipping the entire network with ETCS Level 1 LS by the end of 2017, and
- equipping the entire network with ETCS Level 2 from 2025 onwards.
The challenges:
- Infrastructure use: The SBB’s railway network is being used more and more intensively. Two consequences of this are the in-creasingly tough demands as regards the robustness and performance of the safety installations and the decline in maintenance produc-tivity.
- Multiplicity of systems: Today, there are 16 different types of interlocking system in service, and they have a mean age of 26 years. Increasing networking is making them more susceptible to disruptions, and the work of the personnel is becoming more demand-ing. It is indispensable to provide effective protection for the intensely interlinked system as a whole and to achieve a reduction in sys-tem diversity.
- System costs: From 2020 onwards, the older relay-based interlocking units are going to need replacing at the same time as the first generation of electronic interlocking units as well as eight big interlocking complexes. It is forecast that 65% more money is going to be needed for investments, which makes it essential to reduce overall system costs and to improve the price/performance ratio.
- ETCS migration: Building up ETCS Level 2 with the existing interlocking generations is going to be costly, and, if ETCS Level 2 is implemented in bits and pieces, it is unlikely to produce the desired results on account of the expensive, temporary transitions between levels. If the interlocking functions can be optimised for ETCS, it will then be possible to achieve greater contributions to capacity, safety and reducing the costs of installations.
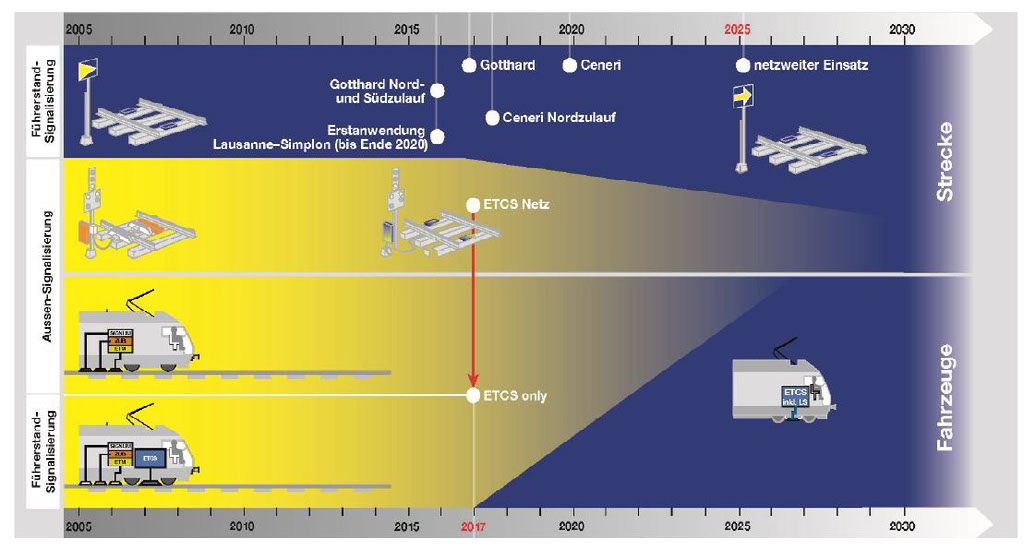
The vision: Complete automation through fast ETCS migration. There is still massive untapped potential in enhancing the degree of auto-mation, eliminating the human factor in production, reducing the costs of replacing interlocking systems, increasing capacity and improving punctuality and precision.
In cooperation with Deutsche Bahn and the ÖBB, the SBB is involved in the NextGen innovation project, which is preparing a new inter-locking platform as a springboard for tackling the forthcoming challenges. The development aim is to have a very lean, powerful and pure-ETCS installation for the indoor part of the equipment. It is planned to introduce it throughout the network by 2035 without needing to make adaptations to the outdoor equipment.
Challenges faced by Austrian Federal Railways (ÖBB)
Dr. Johann Pluy (ÖBB Infrastructure) started his presentation with a challenging vision: “We want to have as many people as possible enthusiastic about the railway”. One thing the ÖBB is doing to achieve that is to make the treasure chest of “data” available for its clients, in other words to improve the use made of the data that arises during operations and thus to enhance customer satisfaction. Another aim, however, is “employees on station platforms” to improve safety and security and to assist the travelling public.
In its command, control and safety systems, the ÖBB too faces the problem of the excessive numbers, diversity and complexity of its installations. That also applies to the system costs, which urgently need to be brought down. The true challenges for the management are, therefore, to maintain an overview, to recognise the relative importance of the systems making up the command, control and safety equipment and to reduce the costs. To be able to do that, it must recognise and evaluate the risk of the technology used and develop technology strategies as well as coordinated plans for migrating from one technology to another. By no means the least point is the deployment of adequately qualified personnel.
In the light of the experience Austria has already had with ETCS, the continuous further development of the technical specifications and the legal framework conditions, a three-phase plan has been defined for the introduction of ETCS:
■ Fundamental strategy:
- position paper containing the requirements, and
- ETCS migration plan up until 2035.
■ Orientation – detailing the special strategy:
- (downwards) compatible, interoperable ETCS,
- including those ETCS projects already decided on,
- revised migration plan up until 2035,
- ensuring the availability of finances, and
- no new Austria-specific ETCS functions.
■ Execution phase:
- use of ETCS in accordance with the migration plan.
It has been observed amongst the five operating control centres that there are differences as to who owns what within the system and also as to size. The aim for the future is to arrive at operating control centres all of a similar size and all owned by the ÖBB. The building up of geo redundant systems and remote workplaces for safety-relevant operations does appear to be feasible, as does the integration of secondary railway lines.
There are two particular innovations that ÖBB Infrastructure is working on:
- INFRA Info-Hub: The aims here are to reduce complexity and unify the interfaces and thus improve the exchange of data with external systems. Infrastructure data for both commercial and non-commercial further use is to be made available through an API inter-face in as near to real time as possible and without discrimination, in the hope of encouraging new information products and services.
- Adaptive train control: Provision of real-time information to support a stable, punctual and energy-efficient operation throughout the entire ÖBB railway network
The strategic concepts for information technology at DB Netz
Dr. Michael Leining (DB Netz) began his presentation by stating that there are elementary differences between DB Netz and companies like Google, Facebook and so on, who are the principal drivers of digitisation. Those trends in digitisation are, however, of only limited relevance for the railway or for signalling systems, but in what direction are they, nonetheless, moving? As long ago as 1942, Joseph Schumpeter described the process of an industrial mutation unstoppably revolutionising the structure of an economy from within, destroy-ing the old structure and creating a new one. The fourth industrial revolution is going to take this process even further still. Here are various theses as far as signalling systems are concerned:
- Digitisation is not the transposition of the analogue world into bits and bytes;
- Big data is not a just a left-over but a critical company asset;
- Automation is only a subset of digital intelligence;
- Digitisation has to be a growth driver, otherwise we do not need it;
- Digitisation must be incorporated in system thinking and not just an offshoot of signalling technology;
- The fundamental idea underlying Industry 4.0 is valid for signalling systems too; and
- We do not need to be afraid of Schumpeter, if we face up to the challenge now.
Digitisation is not limited to technical aspects. The entire business is affected by it. The essential impacts that digitisation has on infra-structure managers are illustrated in Fig. 5. It would, however, be wrong to consider the individual aspects in isolation rather than in a web of interactions. The following examples are given as possible pointers to the direction to be taken:
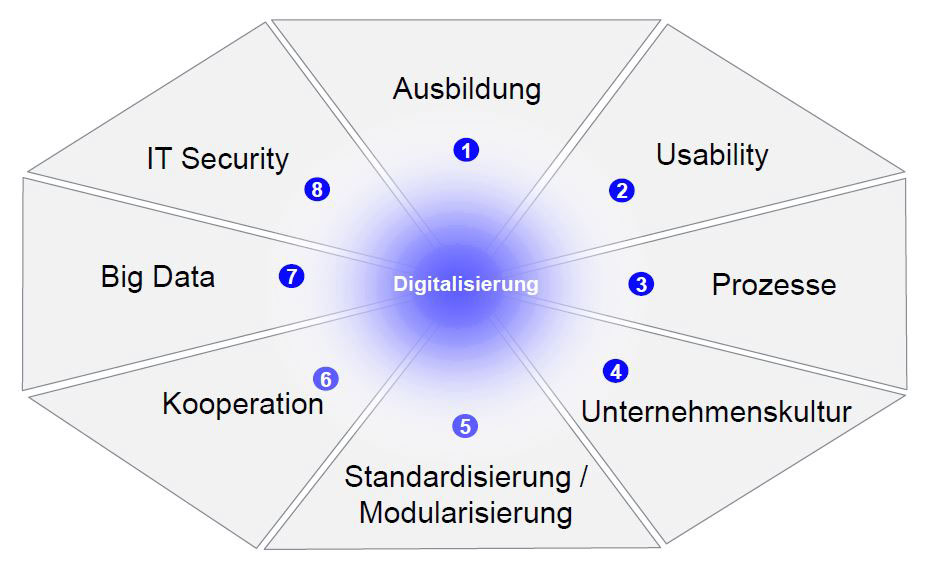
- Very considerable savings through digitisation of the planning processes: The basis for efficiency gains includes a standardised planning model for the exchange of data, a central database for storing the planning data within the operator’s purview and intelligent support with tools in all the planning phases. The benefits to be derived from this are acceleration of the planning processes, improvement of the planning quality, through early detection of errors and avoiding errors at interfaces, and eliminating the need for corrective measures later on.
- Rollout of digital command, control and safety equipment: The systems used are ones with a high degree of redundancy, standard interfaces with a reliable future and integrated operation independent of location. The power supply is kept separate from the transmission of information, but the data networks for the command, control and safety systems and telecommunications are integrated, as are the networks for power supply. That is accompanied by a clear reduction in the number of locations in which technical systems need to be installed.
- Real-time evaluation on the basis of a diagnostic and analytical platform.
- Other projects: These include the use of fibre-optic sensing for various monitoring functions and the establishment of the CYSIS platform for the cybersecurity of safety-critical infrastructures.
New meets old: Challenges regarding training and personnel
Timo Schygulla (DB Netz) began his presentation with a core message: technological change is altering the nature of jobs in command, control and safety systems, making it essential to reconsider qualifications and how to attain them.
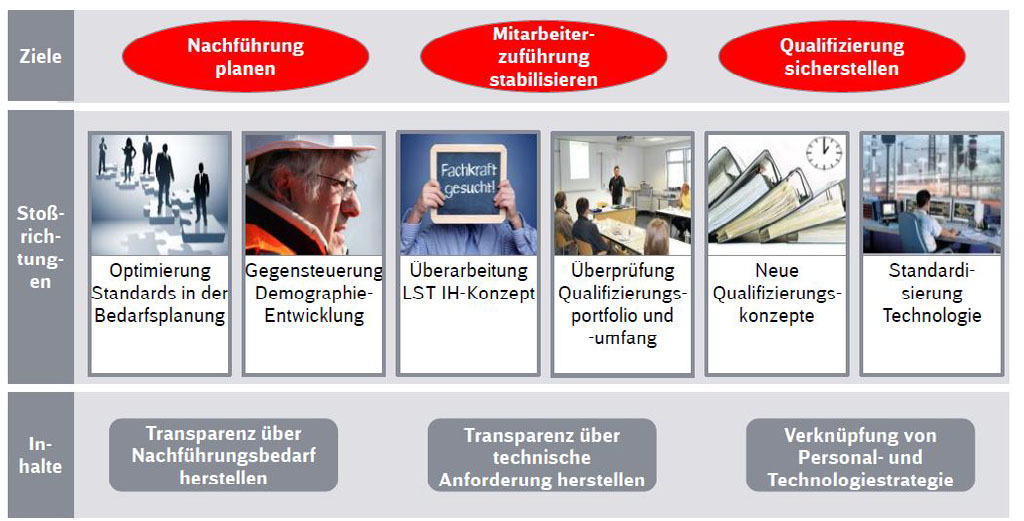
The demographic shift in combination with difficulties in succession planning and obtaining qualifications are causing a continuing loss of knowledge as regards the equipment making up the command, control and safety systems, the telecommunication systems and the 50-Hz electrical equipment, and it is crucial to adopt the appropriate countermeasures. One side to this is that DB Netz’s inventory is going to include a high diversity of legacy technologies for many years to come, while the other side is that successive replacement with modern technology is bringing ever more intensive digitisation and the interlinking of technologies. The changed requirements are markedly altering job descriptions. It is already the case today that there is a growing need for qualifications in the fields of information, communication and network technologies, leading to the recruitment of IT experts rather than specialised electrical engineers. IT is also going to grow in significance for the outdoor installations. Employees are now being recruited from a very limited external market and need complex training to bring them up to the required level of qualification (Fig. 6).
A further challenge is arising out of the above-mentioned professions merging into one another organisationally. One effect of this may be a heavier and broader burden on the employees, unless accompanying measures are put in place. The stress due to the additional workload is already evident today in indicators such as state of health, hours of overtime and staffing for on-call stand-by teams – and that is a situation that is going to get worse, unless there is greater integration of the technologies in new maintenance concepts. Here again, job descriptions need to be adapted and accompanied by the means to instil the corresponding qualifications.
There are further challenges needing to be overcome if employees are to reach the necessary level of qualification at all. These begin with ensuring the appropriate basic qualification of job applicants, of recruiting them and then securing their long-term loyalty to the company. This is indispensable especially where it takes a long time to train employees up to the level of “key qualifications”, in other words acquiring and applying relevant local expertise. Such qualifications represent the starting point for them to be eligible for on-call standby duty. Particular attention needs to be paid here to ensuring the availability and quality of the necessary training measures.
The springboard for mastering these challenges is to establish transparency as regards what the technology requires of employee training. Starting with the job description and robust personnel development planning, it is then possible to determine the training contents and also all the subsequent training measures.
taking the example of electronic interlocking systems
Christoph Jakob (Siemens) began with a reminder that electronic interlocking systems had been in service for some thirty years or so. Deutsche Bahn has now reached its third generation of electronic interlocking systems from Siemens, the Simis-D. A total of more than 300 electronic interlocking units are in operation in Germany, with DB Netz and other railways. The mean age of the electronic interlock-ing units is roughly ten years, and 35% of all switched devices are already operated through them.
The incessant advance in the electronics sector, driven by innovations in semi-conductor technology and by industry-standard compo-nents, is necessitating never-ending adaptations to hardware and software. On top of that comes the need to consider new or amended legal requirements. Given that equipment may remain available for up to fifty years, the network operators’ expectations include maintain-ing the possibility of expanding and converting their system and also a scalable range of functions. Moreover, the interlocking technology ought as far as possible to be based on standard components and/or to satisfy standard interfaces itself.
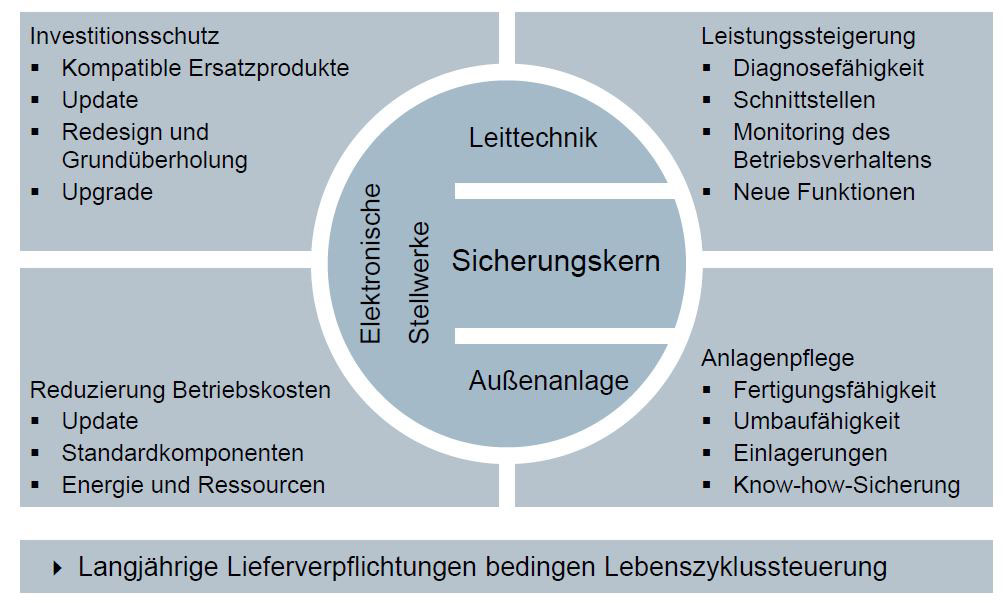
To meet all these requirements, it is going to be necessary to ensure not only that the knowledge is on hand to guarantee the availability of old technologies for as long as possible but also to develop substitute products through innovative solutions, so that they can replace precisely these technologies or, to put it another way, to migrate. One further decisive factor is to keep obsolescence under control, in other words to guarantee the availability of parts for manufacturing and thus also for the supply of spare parts. Migration solutions are the key to being able to meet precisely these requirements and to extending the service life of installations. The regular migration of electronic interlocking systems and/or their components is, however, necessary not only to guarantee the deliverability of substitute solutions but also to make it possible to implement new functions, and to introduce innovative technologies and improved performance. That makes migration solutions into the key factor for both system upkeep and investment protection, and they thus constitute the link between old and new (Fig. 7).
One example of migration is the FTGS track vacancy indication system. Activity here was triggered by the limited availability of subcon-tractor parts for manufacturing the legacy product. The first stage involved buying up and storing those parts that were still available on the market. In parallel with that, development work commenced on a new replacement product. That made it possible to reduce the operation to partial migration only, keeping the outdoor components and the existing basic circuitry. An additional advantage is that the new product takes up less space.
Migration from legacy interlocking systems of the Simis-C type to a state-of-the-art product ready for the future, including the introduc-tion of standard interfaces, was also achieved in four phases.
Field programmable gate arrays
The issue dealt with by Dipl.-Ing. Roland Herzig (Deutsche Bahn) was whether or not the use of field programmable gate arrays (FPGAs) might represent a way out of the obsolescence problem caused by technology cycles. The technical complexity of interlocking systems has inevitably increased with the growing range of functions and centralisation of the operation and installation of computer systems. The move into using off-the-shelf integrated circuits has at the same time meant becoming more dependent on short-lived technology cycles, which did not used to affect command, control and safety systems to that extent in the past. Despite various precautions taken by manufacturers and the railways to guarantee a long service life for interlocking systems, it has to be recognised, in particular, that components for discontinued CPUs have become very costly and labour-intensive and have sometimes even occasioned entirely new developments.
FPGAs are now being considered as a lower-cost alternative. Various applications from the manufacture of signals show that this compo-nent may indeed be helpful. These applications are primarily smallish solutions in subsystems, and their new development and installation has made it possible to replace individual integrated circuits that were no longer available. Examples are:
- replacement of discontinued integrated circuits of the type Motorola MC 146818 in the EBÜT 80 EGL subassembly and the 8085 microprocessor as well as realisation of the ZSB 2000 subassemblies at Scheidt & Bachmann [1],
- use in interface modules for double wheel sensors and in the counting modules of the Pintsch Tiefenbach axle counter,
- use as a chip set in computer subassemblies and as the logic unit in peripheral subassemblies at Siemens, and
- use in various products up to SIL 4 at Thales.
DB Netz is working in cooperation with the SBB and the ÖBB on a project for the partial renewal of the indoor parts of a relay-based in-terlocking system to be based on an “FPGA electronic interlocking unit”. This project is setting out to show:
- that FPGAs are fundamentally suitable as a platform for SlL4 applications;
- that programming or implementation of the protection logic can be done on the basis of the existing relay switches;
- that transformation of relay circuits into FPGA software in an SIL 4 process is possible with FPGA tools; and
- that replacement with next-generation subassemblies can be done at a low cost and with adaptations to the application software and the subassembly design.
The aim is to replicate the indoor part of the equipment with the same functions and thereby to modernise the technology of the interlocking kernel without needing to make changes to either the control console or the outdoor part of the installation (Fig. 8). In later stages, it might be possible to extend the use of FPGAs for the indoor equipment and introduce a new operator’s workstation and new outdoor equipment using NeuPro technology.
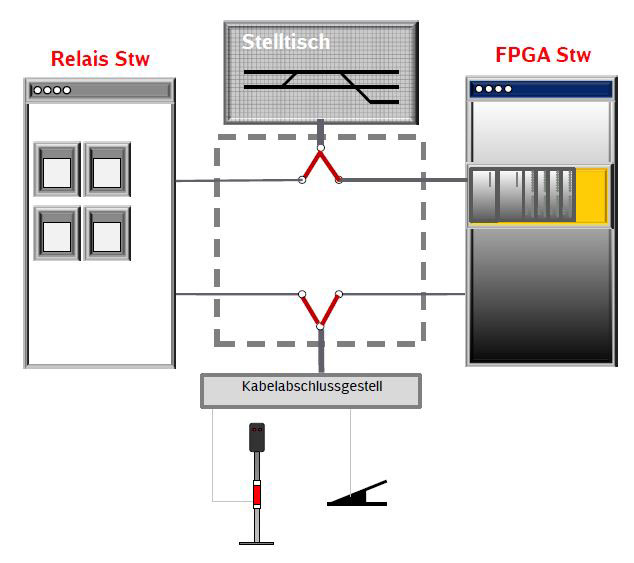
Comments from the audience: It is difficult to emulate the non-volatile states of relays with FPGAs in a current-less state. Relay circuits are, however, very much based on such properties. Roland Herzig’s reply was that that problem had been solved.
Cyber-Security
Germany’s new law on IT security – requirements for transport companies
Dietmar Hilke (Thales Germany) opened his presentation with the statement that “there aren’t any secure IT systems any more”. Modern IT security concepts are based on a broader security paradigm, and merely isolating IT systems is no longer sufficient to make them se-cure, since such systems can be attacked through the interfaces they need. To cope with this wider threat situation, the German legislator has adopted the Federal Act on IT Security. It focuses on two areas:
- the duty to report relevant incidents, and
- minimum requirements for the IT security of IT systems.
The implementing provisions are currently being drawn up. It is expected that two years will be allowed for implementation and also that operators will be required to perform a regular verification of the defined minimum requirements. Furthermore, an “industrial control sys-tem” (ICS) proposed by the German Federal Office for Information Security (BSI) is being considered as the basis for the minimum re-quirements for IT systems.
Operators may feel tempted to regard dealing with security as counterproductive, since operational efficiency and maximum security con-stitute conflicting targets. To ensure that there is a balanced approach to IT security, it is therefore worth aiming for an organisational separation of IT security and IT operation.
The salient features and requirements of an industrial control system differ from those of back-office IT. For that reason, the German Federal Office for Information Security has created an ICS compendium alongside the basic protection concept as the basis for hardening industrial infrastructures. If the threat situation is wider, hardening the systems does not go far enough; it is indispensable to monitor them actively and to take action to ward off attacks. For the practical implementation of these activities, Thales has drawn up a white paper on “Assessing IT security”. It contains the following components as the basis for implementing an IT security system:
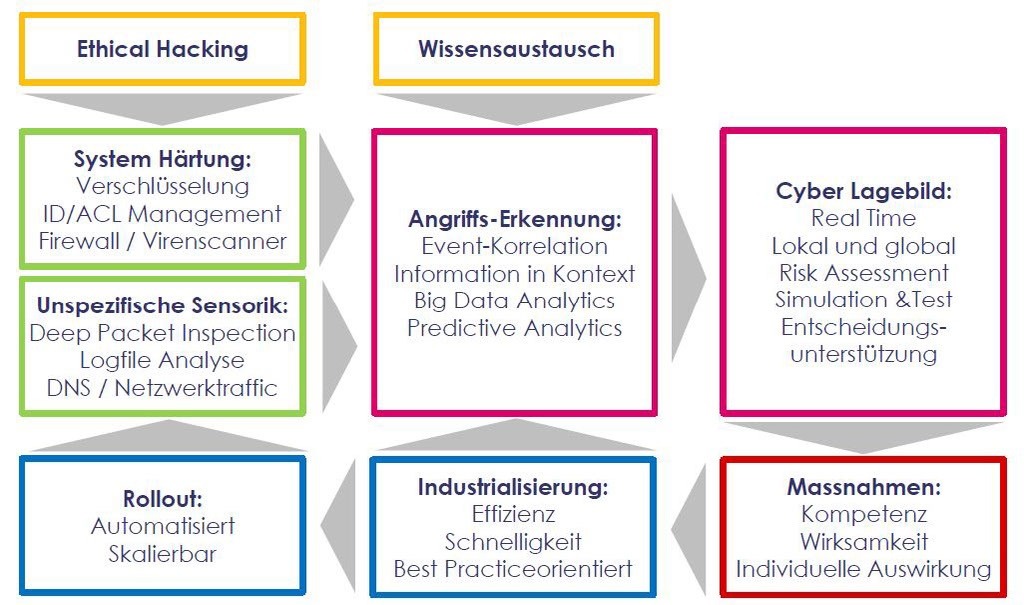
Such a system can be implemented and run by the operator of the IT infrastructure, but does not have to be. Thales has implemented an internationally networked infrastructure, in which the elements contained in the white paper are delivered as “managed security services”. One example of this is that monitoring the technical side of the security of the IT network in the production environment is done by Thales itself as a service in its own computer centre. Once an attack has been detected, Thales organises the combined counterattack and update of the infrastructure. Another possibility is the creation of a managed security service provider for a specific sector. This might be able to bundle the resources needed for complying with the IT security law, considering the special needs of the sector and minimising the overall outlay.
Comments from the audience: There are other security requirements, not just IT ones. In defining managed services, it is essential to determine the nature of the service to be provided very precisely.
Importance of the German Federal Act on IT Security for critical infrastructures, using the railway industry as an example
Andreas Jonas (Bombardier Transportation) stated that the new law placed a duty to set up security measures on the operators of safety-critical systems and infrastructures that are important for society to function. It is a duty that affects both railway operators and infra-structure managers as providers of transport services. Given the fact that the ordinance implementing the Act had not yet been published, it was still unclear which operators were going to have this duty imposed on them. The current assumption was that around 2000 companies would be affected. On the basis of the knowledge available at the time, it was to be assumed that railway manufacturers would not be included directly. They would, however, be required to participate in investigations into incidents and might perhaps also be held liable for weaknesses in their products.
The Act is not comprised of a sequence of instructions on what to do to create security. Its central element is the definition of measures to improve security and to limit the effects if an incident does occur. Milestones in the Federal Act from the Federal Office for Information Security:
- Implementing ordinance with threshold values by the end of 2015.
- Within six months of the ordinance coming into force, a contact point is to be appointed for communication structures for the early detection of crises, for crisis reaction and for crisis management and also for coordinating the teamwork to protect security in the information technology of critical infrastructures in liaison with private industry (§ 8 b III of the Federal Act).
- The Federal Act imposes the duty on operators of critical infrastructures to introduce a minimum standard of IT security measures two years after the ordinance takes effect (§ 8 a I of the Federal Act).
- Once a minimum standard of IT security measures has been introduced, documentary evidence must be submitted at least once every two years to show that the minimum standards are being met (§ 8 a III of the Federal Act). This documentary evidence may be produced through security audits, examinations or certifications.
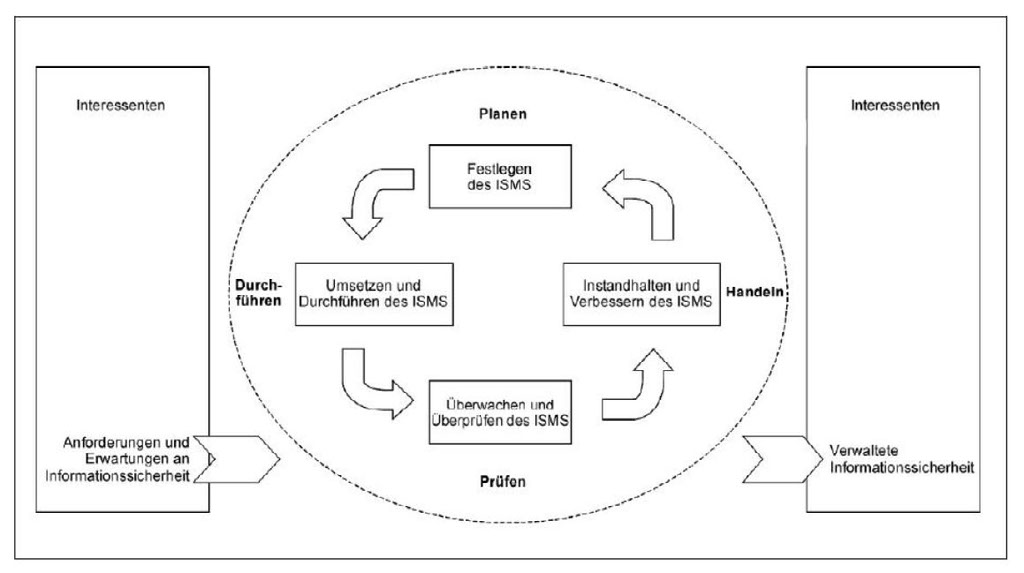
The process set in train by the Federal Act on IT Security is to be a continuous one to keep on detecting weakness and to implement both technical and organisational improvements. The underlying model is going to be similar to the one described in DIN 9001, 2008.
The security concept must encompass various matters, including:
- IT components at the interlocking level,
- IT and telecommunications connections between the interlocking level and the operating control level,
- equipment onboard trains, including the telecommunication networks used (for instance GSM-R),
- passenger information systems,
- ticket sales and reservations systems, and
- door-closing systems.
Implementation is going to involve very considerable process costs. It is estimated that the annual costs of all the necessary paperwork will amount to more than EUR 15 million for the administration and approximately EUR 10 million for manufacturers. Questions of liability in the event of non-compliance have not yet been sorted out, nor has the issue of European harmonisation.
Comments from the audience: The railways expect the manufacturers to support them in complying with the new task. Minimum standards refer to the management system, i.e. to the way in which security incidents are dealt with, and not to technical re-quirements.
Role of IT security in railway operation
Dr. Birgit Milius (TU Braunschweig) turned to the operational aspects of security, which had not been dealt with in the preceding presen-tations.
Rail as a system is comprised of four major segments: the infrastructure, the vehicles, the command, control and safety systems and the railway operation. These system components must work with one another for trains to be able to run. At present, IT security tends to be of rather minor importance for the infrastructure. In the vehicles’ segment and also in the command, control and safety systems, security issues are currently undergoing an intensive examination. The aim is to prevent attacks from succeeding and to be able to detect all at-tacks. Security is, however, not the same thing as safety. Whereas it can generally be assumed that a safe system will remain safe, there can be no such thing as a system that is “once secure, always secure”. The question to be asked, therefore, is what reactions are called for against successful attacks. These reactions must be an integral part of the railway operation and supported by it. The processes and rules that are needed must at the very least:
- intercept those attacks that have not been prevented,
- ascertain attacks that have not been identified through technical means,
- ensure a fast and meaningful distribution of information about attacks within the system, and
- guarantee the safe operation of the railway with a high level of availability even if the condition of the system is uncertain or unknown.
Security as a technical property is not enough! At present, there are obviously only a few activities creating these rules and processes. It is also a topic that has hardly made an appear-ance in railway research to date.
It is the railway’s job to run its operation safely, punctually and economically. The purpose of measures adopted in the event of real or suspected security attacks must be to keep the railway running safely. The rulebook as it exists today does contain fall-back levels for disruptions and irregularities. It must, however, be assumed that it will not be possible to use these in the event of security attacks or only to use them to a limited extent, for instance because it would no longer be possible to satisfy the preconditions implicitly tied up in them. It is also necessary to consider the performance of the fall-back levels. Security attacks may have the effect of limiting the availability of systems without directly endangering the safety of the railway operation. Once again, the processes and responsibilities laid down in today’s rulebook need to be critically questioned. It has to be discussed how train drivers and operations managers are to react in the event of a suspected security attack, and criteria must be established for distinguishing between safety issues and security attacks.
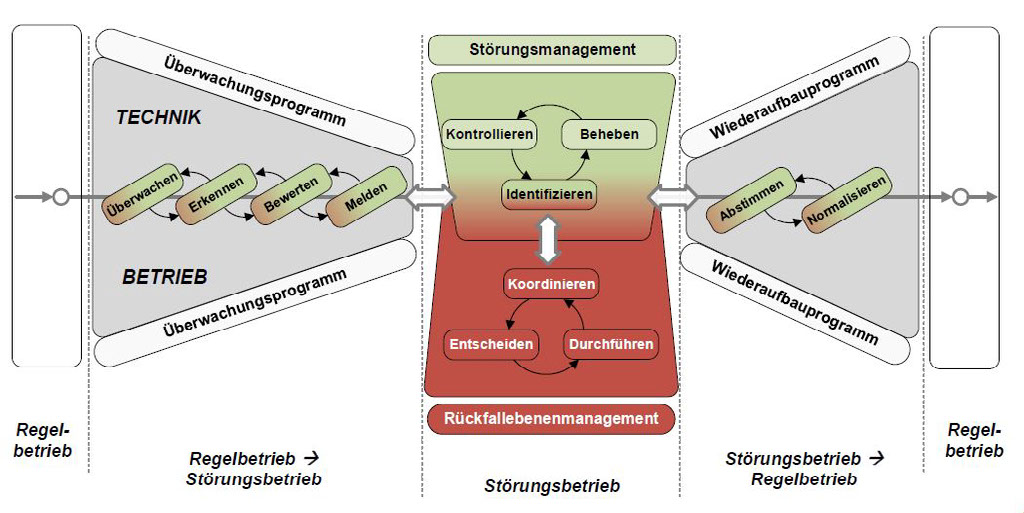
In dealing with questions from the audience, the speaker stressed that the operational rulebook still needed to be meticulously examined to establish how far it would be really feasible to use it in the event of security attacks. Contrary to safety problems, it is impossible to make any statement about the integrity of the displays and the effects associated with them.
IT security: Threat situation in practice
Daniel Schalberger (IT security consultant, Syss GmbH) made a presentation with the title of “Live hacking – how hackers break into IT systems”. He had set up a demonstration of various dangerous situations, configured as a special infrastructure with two PCs connected to one another (a Linux system for the attacks and a Windows system for the victim) and also making use of the internet.
- Manipulation in online shops: The purpose of this demonstration was to illustrate how the prices of items placed in a shopping basket can be manipulated. He explained how the intervention worked on the selected internet page, but it was not possible to perform the manipulation itself.
- Attack on Windows: A manipulated PDF file caused the rather obsolete Adobe Reader to crash on starting and then installed malware on the Windows computer. This established a connection with the attacker’s computer, giving the latter control over the in-fected computer. In the demonstration, the web camera was activated on the Windows computer and its picture transferred to the Linux computer.
- USB Trojan: USB appliances are able to log in as more than one device. In the case in point, the appliance contained a memory stick as well as an invisible automatic keyboard. Windows detected the connected keyboard and linked it up with the operating system. In this way, it is possible to work through any desired sequence of commands and produce a deleterious effect.
- Google hacking: Google supports not only search terms but also so-called search operators. The “filetype” operator can be used to search for filenames with particular extensions. For the special demonstration, Google was instructed to look for the backup copy of a database and its content of user names along with a password (in the form of a hash). In this demonstration the hash was easily decoded.
The operator “inurl: shopping basket” can also be used to look for online shops that use a shopping basket. In this particular demon-stration, manipulation of the shopping basket succeeded.
- Cross-site scripting: If a website has been sloppily programmed it may be possible to smuggle Java script code into it, for instance through a search field. A whole series of harmful manipulations can be performed if the appropriate code is used.
- SQL injection: This form of attack exploits the connection between the webserver and the SQL database behind it. In this situa-tion, SQL is often used to formulate conditions in the URL or in input fields. By manipulating these indications, it is also possible to execute harmful SQL commands.
- WLAN: On many devices the use of WLAN hotspots causes them to remember the names of hotspots they have already used and to look for them regularly. A WLAN stick was connected up to the Windows computer and returned positive replies to all enquiries. It did not take long for a large number of devices to have logged on using all sorts of different hotspot names.
Dipl.-Ing Dirk Krone (Dataport Hamburg), Dr. Christoph Gralla (Alstom Transport), Dr. Michael Leining and Daniel Schalberger gave their views on the topics of “migration and innovation” and “cybersecurity” in a panel discussion chaired by the two chief editors of SIG-NAL+DRAHT. The following are the main points to emerge from the debate:
Digitisation: The panellists all agreed that digitisation is going to bring huge advantages and felt that these were going to impact much more than command, control and safety systems. Deutsche Bahn had launched a competition for ideas and started 260 digitisation initia-tives. DB Netz had arranged a “hackathon”, in which existing data was made available to the participants for them to further process as they saw fit and to generate innovative approaches. Digitisation was important for Dataport too, but it was proceeding with caution.
What was at stake was collection and interpretation of the data. In the case of stationary installations, that was primarily a matter of data of interest for maintenance. As far as IT security was concerned, big data did not differ from other IT systems today, since the threat was similar.
Danish model: The replacement of the entire signalling installation in a single project was very courageous, especially since many adja-cent systems and the operational rulebook needed to be changed at the same time. Given the size of its installation, this would be too big for Deutsche Bahn, but it might make sense for it to carry out faster replacement programmes covering larger territories (such as one region of the network every two-to-three months).
Introduction of ETCS: With introduction in the current form, there was a risk that ETCS might become obsolete before the process was completed. For that reason, the specification had to be implemented consistently and any changes to it needed to be carried out carefully. Components with different development rates had to be kept cleanly separated from one another.
ETCS dialects: It was claimed that there were already fifty national dialects in existence. The industry, however, did not yet see the standard as being in danger, but was eyeing up the dialects with a certain apprehension. DB Netz held the view that the dialects would have to disappear if ETCS was to have a successful future. Both the railways and the manufacturers would have to get by without dia-lects.
HoneyTrain: A Honeypot is an IT system that can be used to trace and analyse attacks. In the “HoneyTrain” simulation a security company had set up an emulation of what it called the train-control system of a metro and then released it for hacker attacks. That the simulation concerned was a railway system was more a matter of chance than anything else [4]. The “control system” was, to be precise, a few servers and a PLC controlling a model railway. Deutsche Bahn did not participate in this simulation and expressed its opposition to the whole idea, since it drew attention unnecessarily to rail as a system.
German Federal Act on IT Security: Security management had been on the agenda at DB Netz for a long time. The effects of the new legislation, which had not yet been finalised, were, however, still unknown. TU Darmstadt and Deutsche Bahn were setting up a new working group on “Cybersecurity for safety-critical infrastructures – CYSIS” to deal with IT and communication security at the interface between trains and the rails on which they run.
Safety meets security – Strategies for documenting evidence
Prof. Dr. Jens Braband (Siemens) quoted Network Rail: “If it’s not secure, then it’s not safe!” Safety and security belong together, but they have differing aims, authorities, terminologies and standards. Up until then, implementation of security had tended to be rather slug-gish, for instance in the form of patching commercial operating systems without obtaining a new approval or by entrusting the task to a service centre in the absence of monitoring networks for anomalies. That was not due to a lack of standards: EN 50129 (IEC 62425) con-tains rules on access protection, EN50159-2 deals with security in communication, DIN V 0831-104 (draft standard) and DIN V 0831-102 (draft standard) have been dealing for years with IT security in command. control and safety systems. The only matter on which work was on-going at that time was IT security for functional safety (Fig. 12). EN 50129 had always had a chapter on “Operation with external influences and access protection”. This standard was currently undergoing a review.
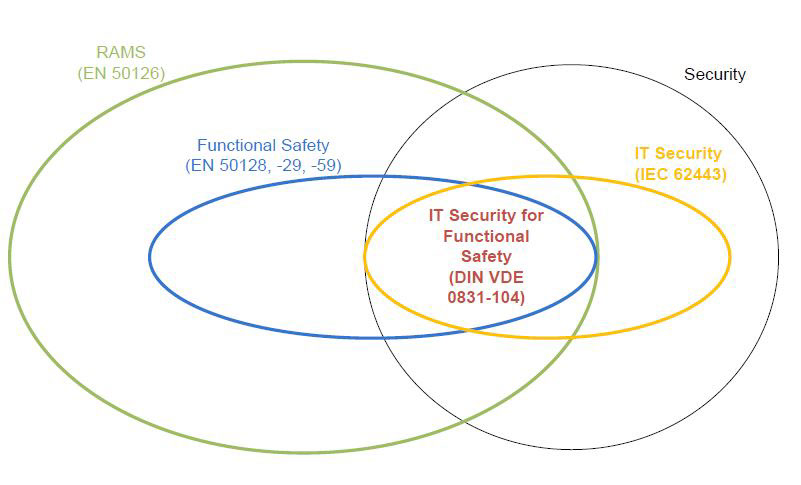
It was impossible to quantify IT security. It was, however, possible for the threat situation to change within a short period of time. For that reason, probabilities were not used for the occurrence of dangerous situations, but rather security levels, which gave some indication of the outlay necessary for making a system secure or, alternatively, for breaking into it. Acceptance of the probability of a threat was based on suppositions and subjective estimates by the user. One way out of this might be to apply the principles of the common safety methods (CSM), because a security problem might turn into a safety problem and the CSM criteria were so general that it would be possible to use them:
- Generally acceptable risk,
- Use of state of the art,
- Comparison with reference systems, and
- Risk analysis.
Practical examples:
- Buying in of certified security components: What matters here was whether the underlying standard might be accepted for the intended use and whether certification was basically recognised at all. It was also necessary to check whether the certificate covered the entire product or only parts of it.
- Protection against malware: Patching the software might eliminate known points of attack, but the approval needed to be renewed every time that was done. One way out of that might be to patch independent safety arguments, but that would be time-consuming and labour-intensive. A further possibility would be to carry out a risk-based assessment of whether to patch or not. That might also turn out to be expensive on account of the necessary frequency. Finally, if the system concerned was a little-used proprietary one, it might be possible to arrive at the conclusion that it would presumably not be a worthwhile target to attack and that it was thus not necessary to patch it.
A member of the audience commented that attacks might also come from inside the systems. Prof. Braband confirmed that that was funda-mentally true, but pointed out that the role management contained in most concepts erected barriers against attacks from within.
Presentations on special topics
New legislation creates the role of registered inspector in the railway industry
Hubert Emmerich (DB Netz), Joachim Stutzbach (VDB) and Katja Schmid (VDB) made a joint presentation on the new function, which closes a gap perceived in the necessary testing and assessment activities. Hubert Emmerich presented the point of view of a railway infrastructure manager, while Joachim Stutzbach dealt with the manufacturers’ standpoint. Finally, Katja Schmid discussed the legal angle. The European Union defines the various roles involved in testing and assessment in the railway sector as follows:
- Notified bodies for performing tests in accordance with TSIs,
- Designated bodies for performing tests in accordance with notified documents, and
- Assessment bodies for assessing risk-management procedures.
These do not, however, cover the entire gamut of testing. For that reason, Germany has created a new role called “registered inspector” (“Prüfsachverständiger)”. This is a person who performs all the testing activities concerning the infrastructure except for those contained in the TSIs and possibly in notified documents. He or she also assesses changes rated as not significant according to the CSM risk assessment.
In future, the activities, rights and duties of registered inspectors as well as their appointment are going to be governed by an ordinance, which already exists in the form of a draft. It lays down that recognition of the profession and the examination linked to that are to be a task for the Federal Railway Authority (EBA). A transitional arrangement makes it possible for recognised experts to continue to do their work. There are two points to which it is particularly worth drawing attention:
- The maximum age for registered inspectors is 68 years. This same limit has so far been indicated in an EBA administrative regulation. It has now become more difficult to authorise exceptions through ordinances. The effect of that might be that the existing bottlenecks in the inspection of installations could deteriorate further.
- The results presented by registered inspectors are being upgraded. The draft ordinance lays down that a “rebuttable presumption of substantive correctness” applies to the outcome of the examination performed by registered inspectors. That releases the EBA from the duty to consider all aspects of a case ex officio, so that it is to become admissible for it to adopt the results of expert inspectors for its administrative acts without verifying them.
One question that arises in particular in the legal appraisal of the draft ordinance is whether, if adopted, it would have implications for the personal liability of future registered inspectors:
- Liability under civil law for harm to persons and damage to property (Fig. 13): Here fault-based tortious liability is fundamentally possible, but of virtually no relevance in practice. The current view is that the presumption of correctness will not lead to any shift to the disadvantage of the registered inspector.
- Liability under criminal law: Here it would be possible to imagine negligent bodily injury or homicide. Once again, there is no indication that there would be any change resulting from the assumption of correctness.
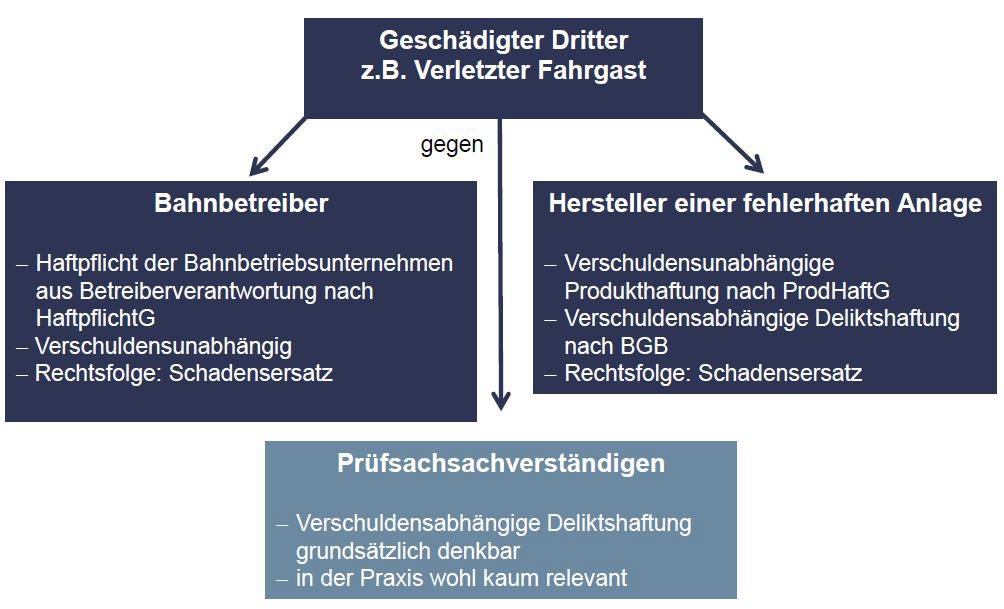
Comments from the audience: In risk assessments, the probability of human failure is taken to be 10-3. If such an instance really does occur, it will be called negligence. Negligence presupposes that the person concerned objectively violated his or her obligation of due diligence. The Austrian Railway Act too used to contain a passage on rebuttable presumption of correctness, but the administrative court struck it out, because decisions that would of necessity have to be taken by authorities were shifted to the private space.
Distributed power provision (DPP) – Flexible power supply as an important element in a decentralised interlocking technology archi-tecture
Oliver Schwehn (Thales Germany) began by examining what sort of power supply would be required by the distributed element. A classical power supply had to fulfil the following functions:
- Power distribution: Getting power to all components in the necessary voltage form.
- Power production: If an uninterrupted power supply is to be guaranteed, batteries, diesel generators and transformers are all of importance. In the distributed structure, photovoltaics and fuel cells are gaining in importance.
- Electrical safety: This heading includes not only the protection of people and installations but also ensuring that there is no feedback affecting the signalling.
- Monitoring: Keeping within the operational parameters calls for monitoring and control. For that reason, diagnostic tools are being increasingly used.
In the conventional architecture, power is fed in centrally. Distributing it to the location of the load and guaranteeing the electrical safety is then the job of the interlocking system.
As a consequence of modularisation, the installation of controller units in the track area is causing a gap to arise in the power distribution between the source and the controller. This is where the concept of “distributed power provision” (DPP) comes in for a supply structure without interruptions. In addition to that, if there is no supply structure, it creates the possibility for power provision that is a perfect fit.
The realisation of protection equipment constitutes a design challenge, given the greater distances involved. The devices usually used today are of only limited suitability. Given that only correctly designed protective equipment is able to guarantee the desired availability, it also has a direct impact on the availability of the entire interlocking installation. Another factor on top of that is that the railway-specific normative requirements applicable along the railway lines are not absolutely essential for equipment inside interlocking buildings. With DPP, it is Thales’s intention to offer a comprehensive concept for supplying power to field elements.
Currently, one field test is being prepared, namely in Hinwil, within the SBB’s infrastructure. The test is being configured with two networks and real cables right next to the track. There are two power feeds. The distribution points provide the connection to the devices needing power (several coloured-light signals and a switch-and-crossing simulator). In addition, there is a bus coupler connecting the two networks. A fault simulator makes it possible to simulate various disruptions.
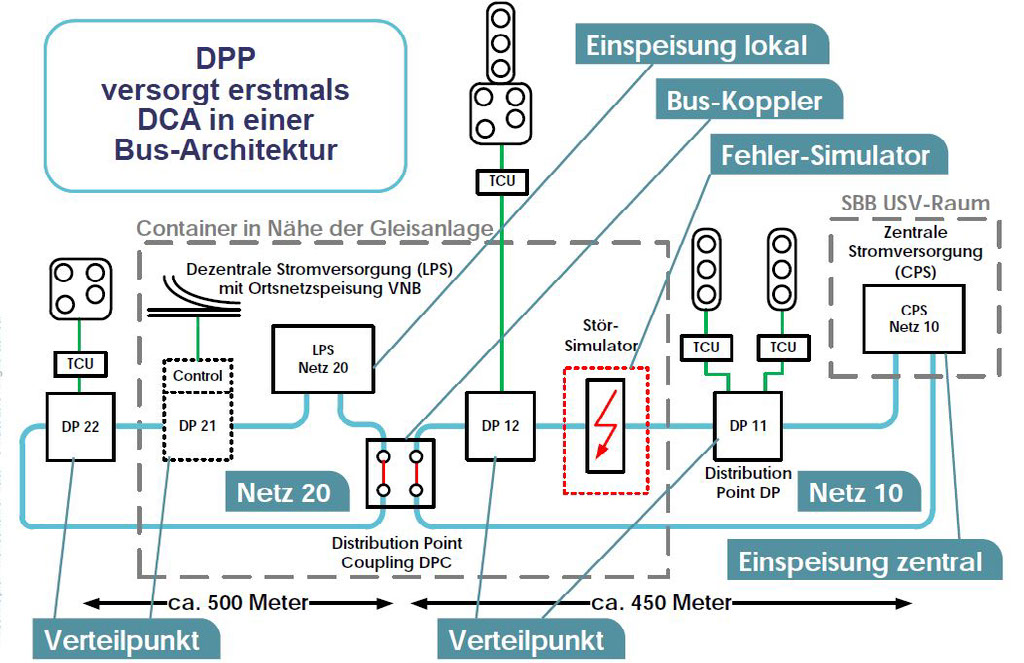
Comments from the audience: Given the large number of switched-mode power supplies distributed throughout the network with their negative characteristic curves, there is a danger of chaotic conditions affecting the power supply. This issue took the discussion back to the question of security. In order to provide protection against attacks coming, for instance, from the diagnostic network, it would presumably be necessary to have recourse to the approaches used in the other parts of the command, control and safety systems.
Fibre-optic sensor systems in the railway environment – opportunities and challenges
The content of this presentation by Max Schubert (DB Netz) was the subject of a recent contribution in SIGNAL+DRAHT. There is thus no need to report on it here.
Concluding remarks
It has to be admitted that the topics of “challenges” and “new meets old” have already been dealt with at various SIGNAL+DRAHT con-gresses. Nonetheless, the presentations contained within this block on this occasion shed new light on a number of interesting aspects. Once again, the challenges appear in the rollout of ETCS (and CBTC too), but at the same time practical experience is playing an increasing role in equipping entire networks. Denmark is an example that is frequently quoted in this respect. A similar situation applies for the modernisation and modularisation of safety equipment. One interesting point to emerge was that, by keeping the “aging relay technology” going through installing FPGAs, it might be possible to create a little more leeway in renewing relay-based interlocking systems no longer supported by their manufacturers. The feasibility of doing that in practice has, however, not yet been demonstrated.
It is interesting to observe that IT security had never been a topic at a previous SIGNAL+DRAHT congress. The explanation for that is most certainly not that there is no IT in command, control and safety systems. Nor is it an issue that is unknown in this sector. The reason for the sudden intense concern with this matter, at least in Germany, is to be found in the new Federal Act on IT Security, which forces the infrastructure operators (and not just them) to take cognisance of the threat and to react to it. Protection through proprietary technology and the use of closed networks is more and more losing its effectiveness with off-the-self components, networks and operating systems making their way into command, control and safety equipment and with the networking of subsystems moving threateningly close to the internet. That dangers lurk in places that would never have been regarded as possible was demonstrated impressively through the live hacking demonstration, although presumably, what the presenter showed was at times no more than a simulation. HoneyTrain too (even if considered to be in bad taste) shows that there are those who are looking for weaknesses. It may well be that the Federal Act on IT Security is going to be an expensive, labour-intensive and time-consuming matter for the operators, but there would be a dramatically higher price to pay if ever there were to be a successful attack on the IT system of a command, control and safety installation, which would have a widespread public impact and attract many imitators.
The real “innovation firework” came right at the end – not the first time that has happened at a SIGNAL+DRAHT congress: fibre-optic sensing. Actually, fibre-acoustic sensing would be a more accurate term, since it is after all acoustic effects that come into play here. The number of possible applications would appear to be unlimited, and it is merely a problem of the appropriate exploitation of the data captured. Just how fascinating the audience found this presentation can perhaps be gauged by the large number of people who queued up to speak to the presenter in person afterwards – a very unusual occurrence for the end of a congress. The really exciting question is: which applications will make their way into practical use and how compatible will they be with the many different variants of railway network?
Thanks to all supporters
